审稿人1
弱点:
- The paper does not describe the attack model clearly other than to state that an adversary can make the traffic violate the network policy … by deleting or adding the forwarding rules of the compromised switches.未描述论文的attack model. (攻击者是怎么让流量违背网络策略的)
- Section III does not describe the network operation well but rather goes into the details of the path validation approach (using the additive magma operation, which is not clearly motivated). 第三节未描述网络操作而描述路径验证方法(使用additive magma的动机未描述) \(ok\)
写得怎么样
- The authors need to present a high level overview of their approach before describing the individual approaches. The paper is difficult to follow. 描述每个方法时要先给出它的整体概念.文章难读懂. (不知道这里他说的"它们的方法"指的是啥)
- Figure 4 is unreadable due to the small text size used. 图4太小了,看不清 \(ok\)
额外评价
- The reader is left with a lot of unanswered questions: How are all the sources programmed to add an extra packet header in the single packet path validation method? How is a flow identified for the network flow path validation method? 读者留下了多未解答的问题, 单包验证算法中所有的源如何被编程到了个额外的包头中的;流路径验证方法中如何去识别一个流. \(ok\)
- On page 8, the following sentence should be rephrased: “The more complex the topology, the more the network flows paths overlap, and therefore the more greatly reducing storage costs for path validation.” 第8页的一句要重写. \(del\)
我的总结
- 添加攻击模型;添加sdn网络基本操作
- 给每部分要讲什么添加个总结性的话
- 图弄大一点
- 根据要求修改,详细说明单包验证,多包验证过程
- 这个作者应该不是这个方向的
审稿人2
论文总结:
- The authors have proposed a(FLPVS (flexible and lightweight path validation scheme) in the context of SDN. The scheme has two parts. Firstly, there is a validation information storing optimization method. Secondly, a path partition scheme in the controller validates the overlapping sub-paths of different network flows. The idea of the path validation scheme framework is similar to the existing related work and the paper lacks the compaarisons with related work. 和已有的工作有点像,未和已有的工作做对比.
缺点:
- The scheme framework is very similar to prior work and the basic idea proposed in the paper is not new. Inaction, the experiments are not comprehensive to compare with related work. 与现有的工作很像, 实验部分未与相关工作做对比.
写得怎么样
- 好
额外评价
- 没给
我的总结
- 添加与相关工作对比实验, 添加与相关工作不同地方说明并做强调, 审稿人应该没看懂
- 基本没给什么意见, 说与现有工作像,没说与哪个像.
审稿人3
缺点
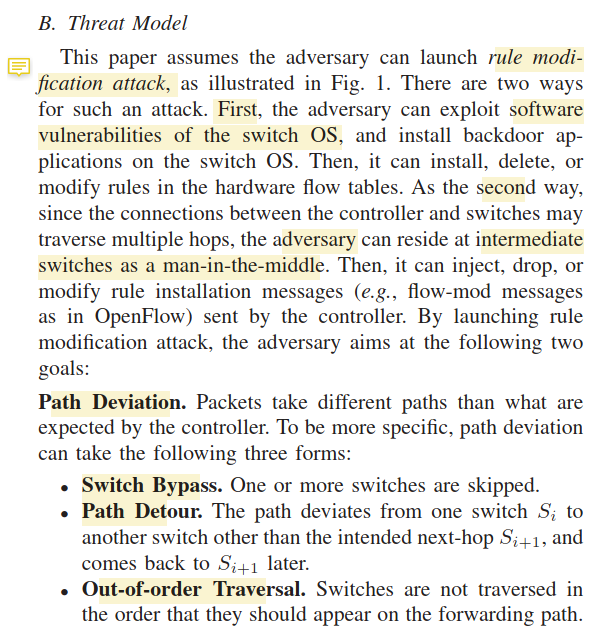
- Security-oriented papers need to have a threat model. The paper lacks a clear specification of the adversary and the components that are controlled by the adversary. The paper does not argue what knowledge the adversary receives, how misinformation can be prevented or detected, or at what point the system fails. 没有threat model, 缺少明确的攻击声明以及攻击者能控制的部分,未说明攻击者所能得到的知识,如何防止或检测错误信息,以及在什么情况下系统会失效
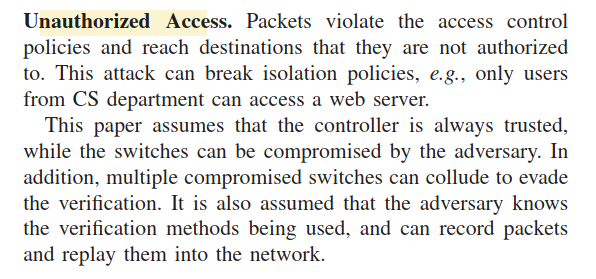
- Notably, Section V does not describe the results of a security analysis. As an obvious scenario, if adversaries control all switches on the path, they could simply not tell the controller about any packets, allowing communication to occur covertly without the controller’s knowledge. If all switches are legitimate, then the attacks describe in the introduction (“deleting or adding the forwarding rules of the compromised switches”) would not occur and the approach would be unnecessary. Accordingly, this approach works when some malicious switches are present, but some non-compromised switches also exist on the path. An analysis on what proportion that can be malicious would be telling. 第五部分没有进行安全地性分析,比如攻击者掌握了这条path上的每一个交换机,那它就可以不给控制器发任何数据包的信息,在转发包时不需要控制器的任何信息. 如果所有交换机都是良性,这个方法就没有必要. 这个方法只有在一条路径上即有良性交换机又有恶意交换机时有效.因此需要加一条分析说明哪部分可以是恶意的.
- The packet marking approach is not new and was proposed for preventing of IP source address forgery in the past. Prior work, such as [Yaar, Abraham, Adrian Perrig, and Dawn Song. “StackPi: New packet marking and filtering mechanisms for DDoS and IP spoofing defense.” IEEE Journal on Selected Areas in Communications 24.10 (2006): 1853-1863.] and [Bremler-Barr, Anat, and Hanoch Levy. “Spoofing prevention method.” Proceedings IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies. Vol. 1. IEEE, 2005.] are not cited, but are seminal works in this area. I am surprised the authors did not compare against those prior marking schemes. 数据包标记方法并不新,有相关文献中已提出但并未引用. 并未与这些方案作比较.
- The performance section is a simulation, but it does not take into account the actual impact of running this system in hardware. SDN switches can perform elevations, yet be terribly slow at it. Likewise, marking in a general-purpose CPU on those switches can incur real performance costs. To truly understand the efficiency of this approach in practice, the evaluation needs to be done empirically. 实验只模拟了,未在真实交换机上跑, 要我在真实交换机上跑出结果.
- The paper does a poor job of guiding a reader through its formalism. In Section III, the first equation is not related to the switch information (S_i, s_i, k_i). Instead, it uses a_1, b1_, a_2, b_2, without relating them to the switch information. The best way to reach an audience is via example that simultaneously walks the reader through the example and intuitively explains the results while simultaneously advancing the formalism. As written, many audiences will struggle to glean insight from Section III. 故事讲得不好, 全文符号统一. 第三节难以深刻理解.
写得怎么样
The writing itself is good. The authors’ use of formalism without explanation makes it extremely difficult to understand their contribution. 写得好,但是公式那块没介绍好
我的总结
- 添加攻击模型
- 添加安全性分析(按意见)
- 看看他说的这两个已有的论文. (没看到这两个论文)
- 要我在真实交换机上跑出结果这个有点办不到了.
- 检查第三节逻辑
- 作者是懂的,但是他根本不想要我的.
攻击模型
- 攻击者能干嘛
- 写本文假设,一条一条的写
- 写SDN基本逻辑, 和2一起写
Efficient Forwarding Anomaly Detection in Software-Defined Networks
PPV Enabling efficient source and path verification via probabilistic packet marking


Network-Wide Forwarding Anomaly Detection and Localization in Software Defined Networks

Verifying Rule Enforcement in Software Defined Networks with REV


Towards Rule Enforcement Verification forSoftware Defined Networks
Dynamic Packet Forwarding Verification in SDN